By: Denise Simon
FoundersCode.com
Vladimir Putin has his propaganda machine working in full speed. We are being sucked into it and not recognizing the clues much less asking harder questions against his agenda.
There is a two part series on the Pro-Kremlin operation. Part 1 video is here. Part 2 video is here.
Now, the movement behind the machine is something called ‘The Agency’ which is a location in St. Petersberg, Russia called the Internet Research Agency.
From DenisonForum: The Agency’s origins can be traced to the 2011 anti-government protests, organized because of the growing evidence of fraud in the Parliamentary elections that year. The protests had been organized largely via Facebook, Twitter, and LiveJournal and the government wanted to ensure that similar protests were far more difficult to put together in the future. So the next year, Vyascheslav Volodin was named the new deputy head of Putin’s administration and given the task of gaining better control over the internet. In addition to starting the Agency, laws were passed that required bloggers to register with the state and the government was allowed to censor websites without a court order. Putin justified the new laws “by calling the Internet a ‘C.I.A. project,’ one that Russia needed to be protected from.”
The full background investigation on the Internet Research Agency, or rather the Kremlin troll factory is found here.
For the software and internet geeks out there, below is the proof of the machine where evidence was peeled back by using open source analytic tools.
From Global Voices Online: In April of this year, Radio Free Europe/Radio Liberty and the Guardian reported on the website вштабе.рф, a large photo gallery of pro-Russian memes and “demotivator” graphics. Most of these crude caricatures ridicule US, Western, and Ukrainian leaders, whilst portraying Vladimir Putin as strong and heroic.
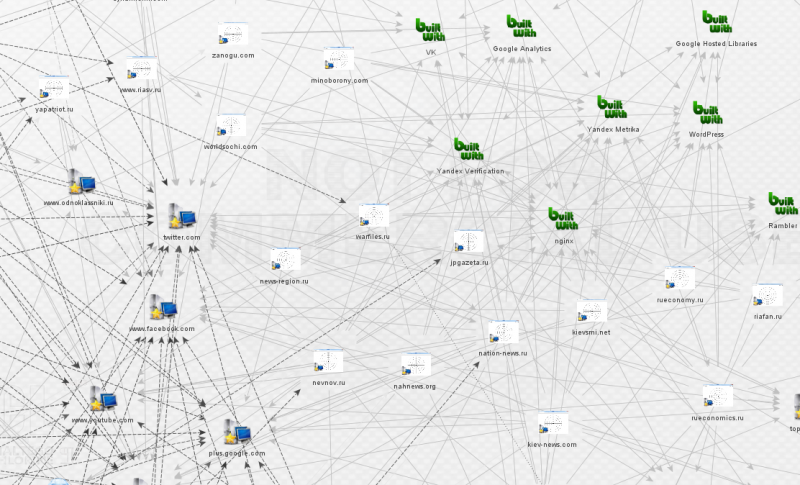
The site gives no credit or attribution for its design, and offers no indication as to who might be behind it. Intrigued by this anonymity, I used Maltego open-source intelligence software to gather any publicly-available information that might provide clues.
The Secrets of Google Analytics
My use of Maltego revealed that the site was running Google Analytics, a commonly used online analytics tool that allows a website owner to gather statistics on visitors, such as their country, browser, and operating system. For convenience, multiple sites can be managed under a single Google analytics account. This account has a unique identifying “UA” number, contained in the Analytics script embedded in the website’s code. Google provides a detailed guide to the system’s structure.
Whilst investigating the network of sites tied to account UA-53176102, I discovered that one, news-region.ru, had also been linked to a second Analytics account: UA-53159797 (archive).
This number, in turn, was associated with a further cluster of nineteen pro-Kremlin websites. Subsequent examinations of these webpages revealed three more Analytics accounts, with additional sites connected to them. Below is a network diagram of the relationships I have established to date.
Most notably, Podgorny is listed in the leaked employee list of St. Petersburg’s Internet Research Agency, the pro-Kremlin troll farm featured in numerous news reports and investigations, including RuNet Echo’s own reports.
Podgorny’s date of birth, given on his public VK profile, is an exact match for that shown in the leaked document.
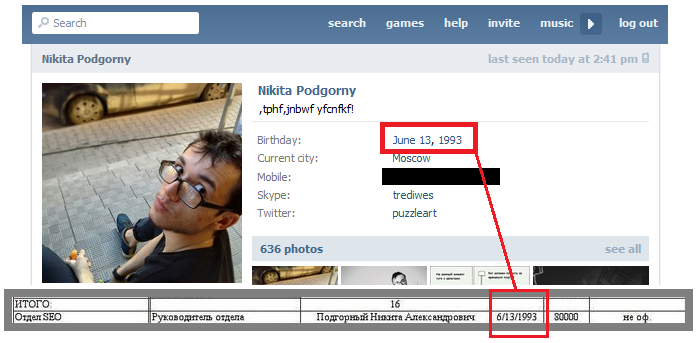
Podgorny is also VK friends with Igor Osadchy, who is named as a fellow employee in the same list. Osadchy has denied working for the Internet Reseach Agency, calling the leaks an “unsuccessful provocation.”
*** This internet researcher will continue the investigation and report more. For expanded details on the first cut of the investigation, click here.
